RADIUS Authentication - NetScaler Gateway 10.5
Navigation
- RADIUS Overview
- Two-factor Policies Summary
- Create Two-factor Policies
- Bind Two-factor Policies to Gateway
RADIUS Overview
For two-factor authentication using Azure Multi-factor Authentication, see Jason Samuel How to deploy Microsoft Azure MFA & AD Connect with Citrix NetScaler Gateway
Citrix CTX125364 How to Configure Dual Authentication on NetScaler Gateway Enterprise Edition for Use with iPhone and iPad
Some two-factor products (e.g. SMS Passcode) require you to hide the 2nd password field. Receiver 4.4 and newer supports hiding the 2nd field if you configure a Meta tag in index.html. See CTX205907 Dual-Password Field Shows in First Authentication When Connecting to NetScaler Gateway from Windows Receiver for instructions.
Two-factor authentication to NetScaler Gateway requires the RADIUS protocol to be enabled on the two-factor authentication product.
On your RADIUS servers, you’ll need to add the NetScaler appliances as RADIUS Clients. When NetScaler uses a local (same appliance) load balanced Virtual Server for RADIUS authentication, the traffic is sourced from the NetScaler SNIP (Subnet IP). When NetScaler uses a direct connection to a RADIUS Server without going through a load balancing Virtual Server, or uses a remote (different appliance) Load Balancing Virtual Server, the traffic is sourced from the NetScaler NSIP (NetScaler IP). Use the correct IP(s) when adding the appliances as RADIUS Clients. And adjust firewall rules accordingly.
For High Availability pairs, if you locally load balance RADIUS, then you only need to add the SNIP as a RADIUS Client since the SNIP floats between the two appliances. However, if you are not locally load balancing RADIUS, then you’ll need to add the NSIP of both appliances as RADIUS Clients. Use the same RADIUS Secret for both appliances.
Two-factor Policies Summary
When configuring the NetScaler Gateway Virtual Server, you can specify both a Primary authentication policy and a Secondary authentication policy. Users are required to successfully authenticate against both before being authorized for NetScaler Gateway.
For browser-based StoreFront, you need two authentication policies:
- Primary = LDAPS authentication policy pointing to Active Directory Domain Controllers.
- Secondary = RADIUS authentication policy pointing to RSA servers with RADIUS enabled.
For Receiver Self-service (native Receiver on mobile, Windows, and Mac), the authentication policies are swapped:
- Primary = RADIUS authentication policy pointing to RSA servers with RADIUS enabled.
- Secondary = LDAPS authentication policy pointing to Active Directory Domain Controllers.
If you need to support two-factor authentication from both web browsers and Receiver Self-Service, then you’ll need at least four authentication policies as shown below.
Primary:
- Priority 90 = RADIUS policy. Expression = REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver
- Priority 100 = LDAP policy. Expression = REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver
Secondary:
- Priority 90 = LDAP policy. Expression = REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver
- Priority 100 = RADIUS policy. Expression = REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver
Create Two-factor Policies
Do the following to create the Two-factor policies:
- Create an LDAP policy/server.
- For RADIUS, on the left, expand NetScaler Gateway, expand Policies, expand Authentication, and click Radius.
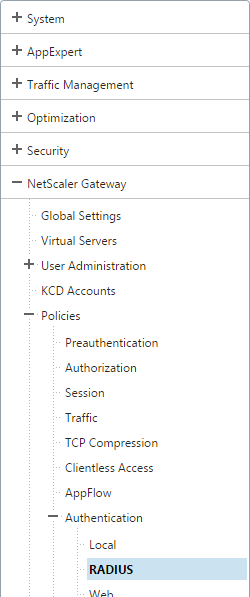
- On the right, switch to the Servers tab. Click Add.
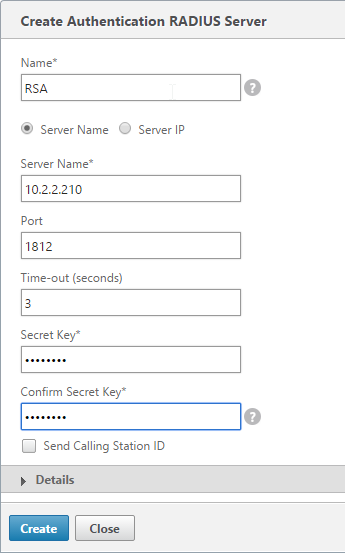
- Give the RADIUS server a name.
- Specify the IP address of the RADIUS load balancing Virtual Server.
-
Enter the secret key specified when you added the NetScalers as RADIUS clients on the RADIUS server. Click Create.
-
On the right, switch to the Policies tab, and click Add.
- Name it RSA-SelfService or similar.
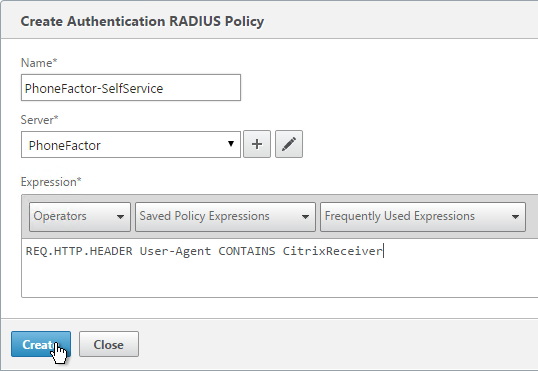
- Select the RADIUS server created earlier.
- Enter an expression. You will need two policies with different expressions. The expression for Receiver Self-Service is HTTP.HEADER User-Agent CONTAINS CitrixReceiver.
-
Click Create.
add authentication radiusPolicy RSA-ReceiverForWeb "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" RSA add authentication radiusPolicy RSA-ReceiverSelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" RSA add authentication ldapPolicy Corp-Gateway-ReceiverForWeb "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" Corp-Gateway add authentication ldapPolicy Corp-Gateway-ReceiverSelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" Corp-Gateway -
Create another policy to match the ones shown below. Both RADIUS policies are configured with the same RADIUS server. The only difference between them is the expression (CONTAINS vs NOTCONTAINS)
Name Expression Server RSA-SelfService REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver RSA RSA-Web REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver RSA 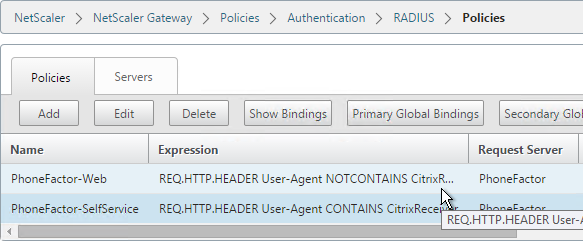
-
Go to NetScaler Gateway\Policies\Authentication\LDAP. On the Policies tab, create two policies with the expressions shown below. Both LDAP policies are configured with the same LDAP server. The only difference between them is the expression (CONTAINS vs NOTCONTAINS).
Name Expression Server LDAP-Corp-SelfService REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver LDAP-Corp LDAP-Corp-Web REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver LDAP-Corp 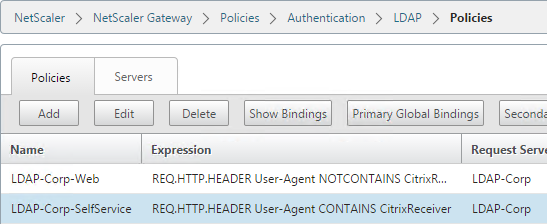
Bind Two-factor Policies to Gateway
-
When you create the NetScaler Gateway Virtual Server, bind the policies as shown in the following table. Priority doesn’t matter because they are mutually exclusive.
Policy Name Type Bind Point LDAP-Corp-Web LDAP Primary RSA-SelfService RADIUS Primary LDAP-Corp-SelfService LDAP Secondary RSA-Web RADIUS Secondary 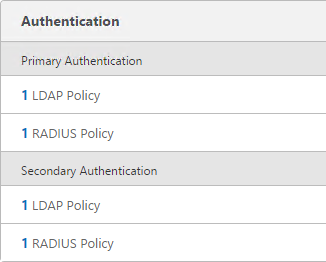
bind vpn vserver gateway.corp.com -policy Corp-Gateway-ReceiverForWeb -priority 100 bind vpn vserver gateway.corp.com -policy RSA-ReceiverSelfService -priority 110 bind vpn vserver gateway.corp.com -policy RSA-ReceiverForWeb -priority 100 -secondary bind vpn vserver gateway.corp.com -policy Corp-Gateway-ReceiverSelfService -priority 110 -secondary -
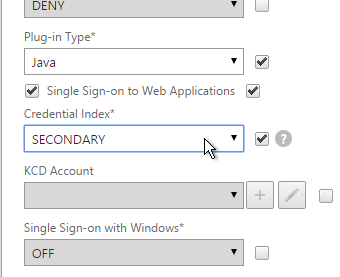
The session policy/profile for Receiver Self-Service needs to be adjusted to indicate which authentication field contains the Active Directory password. On the Client Experience tab or the Session Profile is Credential Index. This needs to be changed to SECONDARY. Leave the session policy for Web Browsers set to Primary.
-
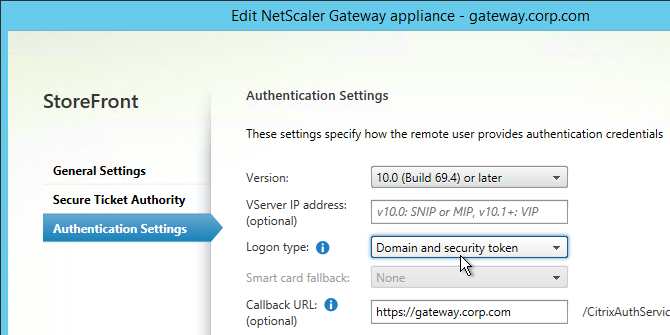
On the StoreFront server, when creating the NetScaler Gateway object, change the Logon type to Domain and security token.